Tech
What is vy6ys? Unveiling the Mystery

The internet is a vast landscape filled with cryptic codes, unfamiliar phrases, and enigmatic terms. “vy6ys” is one such term that might pique your curiosity, leaving you wondering about its origin, meaning, and potential applications. This article delves into the world of “vy6ys,” exploring its possible interpretations and offering insights into its usage.
No Definitive Meaning
Unfortunately, there is no single, universally accepted definition for “vy6ys.” Our exploration through various online resources and databases yields no concrete results. This lack of a clear meaning makes it difficult to pinpoint the exact nature of “vy6ys.” However, several possibilities emerge when we analyze the term’s structure and potential contexts.
Possible Interpretations
-
Code or Abbreviation: “vy6ys” could be a code or abbreviation used within a specific community, online forum, or gaming platform. These codes are often created as a form of shorthand or insider language to convey specific meanings or references. Without further context about the community or platform where “vy6ys” originated, it’s challenging to decipher its exact meaning.
-
Username or Handle: The combination of letters and numbers in “vy6ys” suggests it could be a username or online handle adopted by an individual on social media platforms, gaming services, or online forums. Usernames are often unique identifiers chosen by users to represent themselves in the online world.
-
Placeholder Text: In some instances, “vy6ys” might be a placeholder text used during website development or software creation. Placeholder text, also known as lorem ipsum, is temporary content that fills space until the actual content is added. Developers often use nonsensical strings of letters and numbers as placeholder text.
-
Random String: It’s also possible that “vy6ys” is simply a random assortment of letters and numbers with no specific meaning or purpose. Random strings can be generated for various reasons, such as creating unique identifiers or testing purposes.
Exploring Usage Patterns
To gain a better understanding of “vy6ys,” let’s examine potential usage scenarios:
- Online Games: If “vy6ys” appears within the context of online games, it could represent a specific item, character ability, or in-game code. Consulting online gaming forums or communities associated with the game in question might reveal the meaning behind “vy6ys.”
- Social Media: If you encounter “vy6ys” on social media platforms, it could be someone’s username or handle. Searching for the term on the specific platform might lead you to the user’s profile.
- Software Development: If you come across “vy6ys” during software development or website creation, it’s likely a placeholder text that will be replaced with actual content later.
The Importance of Context
As you can see, the meaning of “vy6ys” hinges heavily on context. Without understanding the context in which you encountered the term, it’s nearly impossible to determine its exact significance.
Searching for Answers
If you’re determined to unravel the mystery behind “vy6ys,” here are some strategies you can employ:
- Search Engines: Utilize search engines like Google or Bing to see if “vy6ys” yields any relevant results. Look for websites, forums, or online communities where the term appears. The surrounding content might offer clues about its meaning.
- Online Dictionaries: Although unlikely, some specialized online dictionaries or jargon repositories might have an entry for “vy6ys.” These resources can be helpful for deciphering codes, abbreviations, or technical terms used in specific online communities.
- Online Forums: If you suspect “vy6ys” is related to a particular online game or platform, search for relevant forums or communities associated with that platform. Community members might be familiar with the term and shed light on its meaning.
Remember: When searching online, be cautious of unreliable sources or websites that promote malware or scams. Stick to reputable websites and forums for accurate information.
FAQs about vy6ys
Q: Does vy6ys have a specific meaning?
A: No, there is no universally accepted meaning for “vy6ys.” It could be a code, username, placeholder text, or simply a random string of letters and numbers.
Q: How can I find out what vy6ys means?
A: The meaning of “vy6ys” depends on the context in which you encountered it. Consider searching online using search engines or exploring relevant online forums or communities.
Q: Is vy6ys dangerous?
A: “vy6ys” itself is not inherently dangerous. However, if you encounter it on a suspicious website or receive it from an unknown source, proceed with caution. It’s always best to avoid clicking on links or downloading files from
elving Deeper: Potential Applications of “vy6ys” (hypothetical scenarios)
While a definitive meaning for “vy6ys” remains elusive, exploring hypothetical scenarios can spark our imagination and shed light on its potential applications. Here are some creative ways “vy6ys” could be used:
1. Fictional Universe
- Invented Language: “vy6ys” could be part of a constructed language within a fictional world, book series, or video game. Fantasy and science fiction authors often create unique languages for their fictional races or cultures. “vy6ys” might represent a word, phrase, or concept specific to that language.
- Alien Communication: Perhaps “vy6ys” is a fragment of an alien language intercepted by radio telescopes or captured through deep space exploration. Deciphering such messages could hold the key to understanding extraterrestrial civilizations.
2. Coding and Programming
- Variable Name: In the world of programming, “vy6ys” could be a variable name chosen by a developer. Variable names act as containers that store data within a program. While programmers typically use descriptive names for better readability, some might opt for shorter or seemingly random strings like “vy6ys” for specific purposes.
- Secret Message: “vy6ys” could be a part of a steganographic code embedded within a program. Steganography is the art of hiding information within another medium, such as hiding a message within an image file. Decoding such messages might require specialized tools and techniques.
3. Art and Music
- Abstract Art: “vy6ys” could serve as the title or inspiration for a piece of abstract art. Abstract art focuses on form, color, and composition rather than depicting realistic objects or scenes. The artist might use “vy6ys” to evoke a particular feeling or concept through their artwork.
- Musical Motif: In the realm of music, “vy6ys” could be a musical motif or a recurring sequence of notes used within a composition. The way the motif is played and manipulated throughout the piece can create a sense of unity and structure.
4. Social Commentary
- Hashtag or Slogan: “vy6ys” might be adopted as a hashtag or slogan within a social media campaign promoting a specific cause or raising awareness about an important issue. Hashtags help categorize social media content and spark conversations around a particular topic.
- Art Movement: “vy6ys” could become the name of a new artistic or cultural movement that challenges traditional norms and explores unconventional forms of expression. Art movements often emerge in response to social or political events, pushing boundaries and sparking dialogue.
Remember: These are just hypothetical scenarios. The true meaning and application of “vy6ys” remain open to interpretation.
The Power of the Unknown: Why “vy6ys” Matters
The mystery surrounding “vy6ys” highlights the power of the unknown. It sparks our curiosity, compels us to seek answers, and ignites our imagination. In a world saturated with information, “vy6ys” stands out as a reminder that there are still things we don’t understand.
The quest to decipher “vy6ys” is a microcosm of the human desire to explore, discover, and make sense of the world around us. It encourages us to think critically, consider different perspectives, and delve deeper into the unknown.
Conclusion
“vy6ys” may not have a single, definitive meaning, but it serves as a springboard for exploration, creativity, and critical thinking. The possibilities surrounding its meaning and application are vast, limited only by our imagination. So, the next time you encounter “vy6ys,” don’t dismiss it as meaningless. Embrace the mystery, and see where your curiosity takes you. You might just discover something new and unexpected.
Tech
Difference Between LED and LCD: Which Display Technology Is Better in 2025?
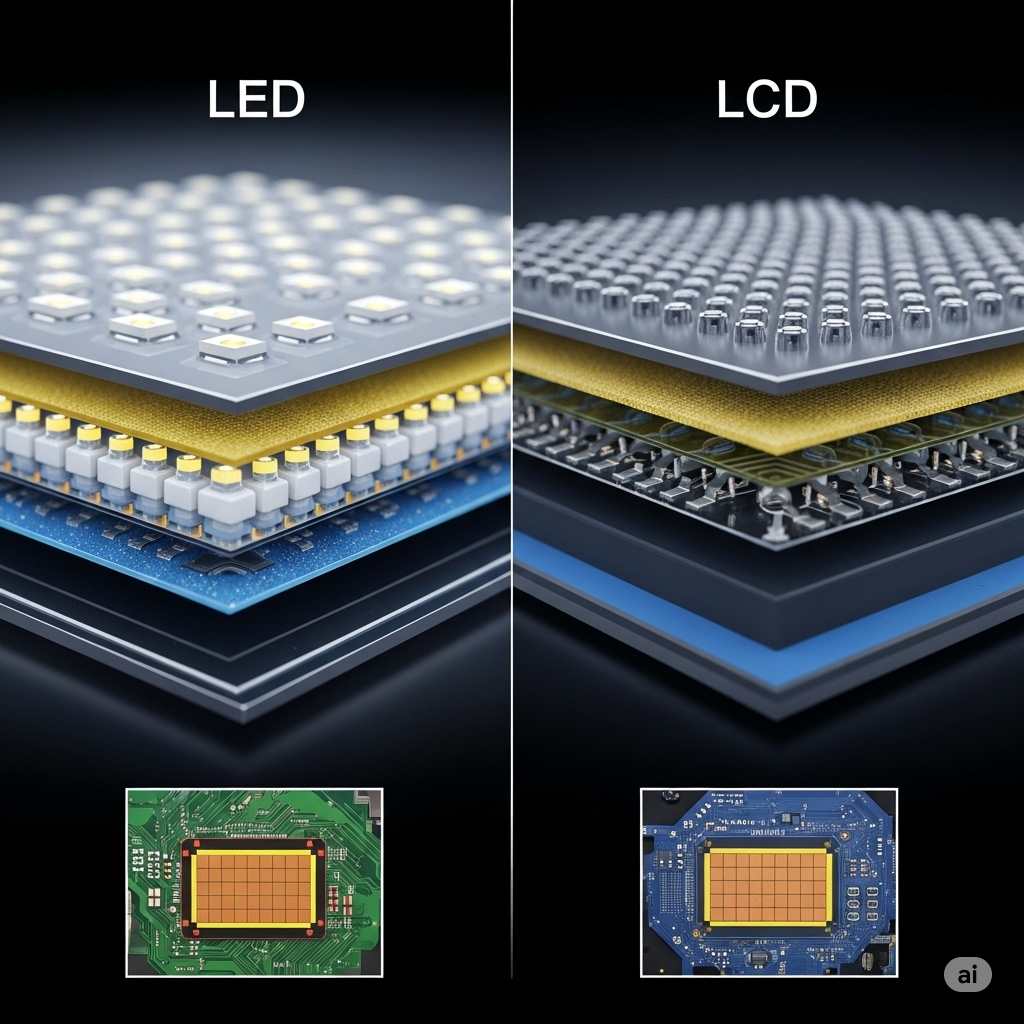
📺 Introduction
In today’s digital world, choosing the right screen technology can make a big difference in your viewing experience. Whether you’re buying a new TV, monitor, or smartphone, you’ll likely come across two common display types: LED and LCD.
But what exactly is the difference between LED and LCD? And which one should you choose in 2025?
This article breaks it down in simple terms so you can make an informed, tech-savvy decision. We’ll also explore advanced display variations and key considerations to help you choose the right screen for your home, office, or gaming setup.
🔍 What is LCD?
LCD stands for Liquid Crystal Display. It uses liquid crystals sandwiched between two layers of glass or plastic and a backlight to produce images.
How it works:
- Light from a fluorescent lamp (usually CCFL) passes through a polarizing layer.
- Liquid crystals manipulate the light to form images.
- A color filter adds color to the grayscale images formed by the crystals.
Key Features:
- Requires fluorescent backlighting
- Produces images by filtering light through liquid crystals
- Commonly found in budget TVs, monitors, calculators, digital watches
Pros:
- Low production costs
- Good for general use
- Energy efficient compared to older tech like CRT
Cons:
- Weaker contrast and color accuracy
- Slower response times
- Less energy efficient than LED
💡 What is LED?
LED stands for Light Emitting Diode, and LED displays are a subset of LCD technology that uses LED backlights instead of CCFLs.
How it works:
- A panel of white or RGB LEDs emits light behind or on the edge of the LCD panel.
- Provides more precise lighting and dynamic contrast.
Types of LED Displays:
- Edge-Lit LED: LEDs placed along the edges; allows for thinner displays.
- Full-Array LED: LEDs placed evenly behind the panel for better contrast.
- Mini-LED (2025 trend): Uses thousands of tiny LEDs for sharper brightness control.
Pros:
- Slimmer designs
- Higher brightness and contrast
- Greater color accuracy and energy efficiency
- Longer lifespan than standard LCDs
Cons:
- Costlier than LCDs
- Edge-lit models may have uneven lighting
🆚 LED vs LCD: Key Differences
| Feature | LCD | LED |
|---|---|---|
| Backlighting | CCFL (fluorescent) | LED (light-emitting diode) |
| Brightness | Moderate | High |
| Energy Efficiency | Medium | High |
| Color Accuracy | Average | Better |
| Lifespan | Shorter | Longer |
| Viewing Angles | Narrower | Wider (especially IPS LEDs) |
| Cost | Lower | Slightly higher |
Learn more about emerging display technologies and their applications at SpaceCoastDaily.co.uk
📱 Advanced Variants to Consider in 2025
🔹 QLED (Quantum Dot LED)
- Developed by Samsung
- Uses quantum dots to improve color range and brightness
- Better than LED in terms of vibrancy
🔹 OLED (Organic LED)
- Individual pixels emit light (no backlight needed)
- Excellent black levels, contrast, and ultra-slim design
- More expensive, used in high-end TVs and smartphones
🔹 Mini-LED
- Offers better control over dimming zones
- Reduces halo effects and improves dynamic range
- Becoming mainstream in high-end monitors and TVs
These technologies often build upon LED panels, offering better performance at a higher price.
📊 Use Cases: Which One Is Better for You?
📺 For Watching TV
- LED TVs are ideal due to better brightness, energy use, and sleek designs.
- Go for Full-Array LED for optimal movie experience.
💻 For Office Work
- LCD monitors are sufficient for word processing, browsing, and spreadsheets.
- LED provides less eye strain over long periods — recommended.
🎮 For Gaming
- LED monitors with high refresh rates and low response times are superior.
- Avoid basic LCDs due to ghosting and lag.
📱 For Smartphones/Tablets
- LED and OLED dominate the mobile space due to high-quality visuals and efficiency.
🧠 Final Thoughts
While LCD and LED both belong to the same display technology family, LED is significantly superior in most categories that matter to users today — including brightness, energy use, durability, and visual quality.
In 2025, unless you’re shopping on a very tight budget, LED should be your default choice. However, be aware of more advanced options like Mini-LED or OLED if your usage includes creative work, high-end gaming, or home cinema setups.
Looking for more tech comparisons and practical guides? Visit SpaceCoastDaily.co.uk for regularly updated articles and smart recommendations.
❓FAQ: LED vs LCD
Q1: Is LED better than LCD?
Yes. LED is generally better due to its superior brightness, contrast, and energy efficiency.
Q2: Do LED TVs last longer than LCD?
Yes, they tend to have longer lifespans and better reliability.
Q3: Are LED screens more expensive?
Slightly, but they offer better value over time.
Q4: Can I use an LCD monitor for gaming?
Yes, but modern LED monitors are much better suited for gaming due to faster refresh rates.
Q5: Is OLED the same as LED?
No. OLED is a different, more advanced technology that offers individually lit pixels and deeper blacks.
Q6: What is Mini-LED and should I consider it?
Mini-LED is a newer version of LED offering improved contrast and brightness. It’s ideal for professionals and enthusiasts.
Tech
DIY Solar Panel Setup for Home: Save Energy & Money

🌞 Introduction
Want to cut down your electricity bills and reduce your carbon footprint? A DIY solar panel setup for home might be the solution you’re looking for. With solar technology becoming more affordable and efficient, more homeowners are turning to solar power as a long-term investment in sustainability.
In this guide, we’ll break down everything you need to know about setting up a solar panel system yourself—from equipment selection to installation and maintenance. Whether you’re a total beginner or somewhat handy, you’ll walk away ready to go solar, save money, and take control of your home’s energy use.
⚡ Why Choose a DIY Solar Panel Setup for Home?
💰 Cost Savings
One of the biggest advantages of going DIY is saving on labor costs. Hiring professionals can cost thousands, while a DIY setup significantly lowers your total investment.
🌱 Environmental Impact
Solar power is clean and renewable. A typical home system can reduce 3 to 4 tons of carbon emissions annually.
💡 Energy Independence
Producing your own electricity reduces dependence on utility companies and protects you from rising energy prices.
🧰 What You Need for a DIY Solar Panel Setup
Before diving into the installation process, gather these key components:
1. Solar Panels
-
Choose monocrystalline for higher efficiency.
-
Polycrystalline is cheaper but slightly less efficient.
2. Inverter
-
Converts DC (from panels) into AC (for your home).
-
Types: String inverter, microinverters, hybrid inverters.
3. Charge Controller
-
Regulates voltage and current from panels to batteries.
-
Prevents battery overcharging.
4. Battery Bank (Optional but Recommended)
-
Stores excess power for use during night or outages.
-
Lithium-ion batteries are ideal but expensive.
5. Mounting System
-
Roof mounts or ground mounts, based on your space.
-
Ensure they’re durable and weather-resistant.
6. Wiring and Connectors
-
Solar-grade cables (MC4 connectors recommended).
-
Proper fuses and circuit breakers for safety.
7. Net Meter (Optional)
-
For grid-tied systems to earn credit on your power bill.
🛠️ Step-by-Step: How to Install DIY Solar Panels at Home
🔍 Step 1: Assess Your Energy Needs
-
Review your electricity bills (monthly kWh usage).
-
Decide whether to go off-grid, grid-tied, or hybrid.
📐 Step 2: Site Evaluation & Solar Access
-
Use tools like PVWatts or Google Project Sunroof.
-
Ensure your roof gets at least 5-6 hours of direct sunlight daily.
🧮 Step 3: Calculate System Size
-
Average home uses ~900 kWh/month.
-
A 5 kW system (~15-20 panels) usually covers this.
🛒 Step 4: Purchase Equipment
Buy from trusted suppliers with warranty options. For top-tier solutions, check out Circle Solar, a leader in sustainable solar energy solutions.
🔧 Step 5: Install Mounting & Panels
-
Attach the mounting system to your roof or ground.
-
Secure panels onto the racking system.
🔌 Step 6: Connect Electrical Components
-
Wire panels → charge controller → battery bank → inverter → home grid.
-
Ensure all safety disconnects and grounding are in place.
📋 Step 7: Inspection & Activation
-
Get local authority inspection if required.
-
Turn on the system and monitor output via your inverter app or meter.
🔄 Maintenance Tips for Long-Term Efficiency
-
Clean panels 2-3 times a year to remove dust and debris.
-
Check wiring annually for signs of wear or corrosion.
-
Monitor performance with apps or online dashboards.
🧠 Pro Tips for DIY Success
-
Start small: Begin with a portable or single-panel system if you’re new.
-
Take safety seriously: Wear protective gear and follow all electrical codes.
-
Consult your utility provider: Especially for grid-tied systems.
🌐 Real-World Success: Why People Are Going Solar
More and more UK residents are adopting DIY solar power to fight rising energy costs and embrace a sustainable lifestyle. Platforms like Space Coast Daily regularly feature success stories and resources on renewable energy—proving that the solar movement is thriving.
✅ Conclusion: Ready to Harness the Sun?
Installing a DIY solar panel setup for home is not just a trend—it’s a smart investment in your future. With the right tools, planning, and guidance, you can generate your own clean electricity and gain true energy independence.
So, are you ready to start your solar journey? Bookmark this guide, explore Space Coast Daily for the latest in sustainable energy trends, and consider checking out Circle Solar for premium components that last.
❓ FAQ: DIY Solar Panel Setup for Home
Q1: Is it legal to install solar panels myself?
A: Yes, in most regions, DIY installations are legal. However, check your local codes and permit requirements.
Q2: How much does a DIY solar system cost?
A: Expect to spend between £3,000 to £6,000, depending on system size and quality.
Q3: Can I run my entire house on solar?
A: Yes, with a properly sized system and battery backup, you can power your whole home.
Q4: How long do solar panels last?
A: Most panels come with a 25-year warranty and can last even longer with proper care.
Q5: Do I need batteries for my solar system?
A: Batteries are optional but useful for off-grid setups and backup during outages.
Tech
What is Janitor AI? Features, Use Cases & How to Use It Safely in 2025

📝 Introduction
Artificial intelligence is rapidly transforming how we interact online, and Janitor AI is one of the most buzzed-about names in the chatbot space—especially for users looking for customizable, conversational, and even NSFW AI interactions.
Whether you’re exploring it for entertainment, roleplay, or productivity, this guide covers everything you need to know about Janitor AI in 2025—from how it works, its features, limitations, and even the controversy surrounding it. If you’re curious, cautious, or ready to dive in, this is your ultimate reference.
🤖 What is Janitor AI?
Janitor AI is an advanced AI chatbot platform that allows users to interact with a variety of characters—ranging from anime-style bots to customizable virtual personalities. Unlike traditional AI chat tools, Janitor AI focuses heavily on character roleplay, storytelling, and human-like interaction.
Many users have been drawn to the platform due to its allowance (at times) for NSFW (Not Safe For Work) conversations, making it popular among adult users. However, its capabilities extend beyond that.
🔹 Key Features:
-
Character-based AI chats (custom bots)
-
NSFW and SFW modes (optional)
-
GPT-based responses (OpenAI or Kobold API supported)
-
Voice synthesis (in some versions)
-
Public character library
📌 Janitor AI Use Cases in 2025
Despite the controversy, Janitor AI is being used for several legitimate and interesting purposes:
1. Roleplay & Storytelling
Writers and fans use the platform for:
-
World-building
-
Character interaction testing
-
Generating dialogues for scripts and comics
2. Entertainment & Fun
-
Anime fan chats
-
Simulated romantic convos
-
Gaming companion bots
3. Mental Health & Venting
Some users engage with soft-spoken bots to:
-
Simulate therapy
-
Talk out problems
-
Seek non-judgmental conversation
4. Productivity Simulation
-
Practice job interviews
-
Language learning through simulated chats
-
Train customer service interactions
🛠️ How Janitor AI Works
Janitor AI is not powered by its own LLM (Large Language Model). Instead, it connects with external APIs like:
-
OpenAI (ChatGPT) – for safe, filtered interactions
-
KoboldAI or Pygmalion – for unfiltered/NSFW content
-
Local Models (e.g., SillyTavern) – for privacy-focused chats
To use Janitor AI:
-
Sign up and login at [janitorai.com] [EXTERNAL LINK]
-
Choose a character from the public library or create your own.
-
Connect an API key (OpenAI or KoboldAI).
-
Start chatting with the bot of your choice.
⚠️ Note: You must configure API settings correctly. Many users get errors if APIs are not linked.
🚫 NSFW & Content Safety: The Big Debate
One of the reasons Janitor AI became viral is because it allowed NSFW chats, especially using Pygmalion or OpenRouter APIs.
However, this has sparked massive debates online, especially around:
-
AI ethics
-
Age restrictions
-
Content moderation
In 2024-2025, Janitor AI removed direct NSFW support on its main platform, but users still bypass this using external APIs or local installations.
🔒 Tips for Safe Use:
-
Use a local model if privacy is a concern.
-
Never share real personal data.
-
Check if the bot creator has moderation settings enabled.
-
Keep SFW mode on if under 18 or in public/shared devices.
📈 Why Janitor AI is So Popular in 2025
| Reason | Description |
|---|---|
| Customizable Bots | Create your own characters with unique personalities |
| Roleplay Freedom | Many bots simulate romantic or fantasy dialogues |
| Easy to Use | No coding needed, simple UI |
| Cross-Platform | Use in browser, Discord bots, or third-party apps |
| Large Community | Public bots, shared prompts, guides available |
🔄 Janitor AI Alternatives (2025)
If Janitor AI doesn’t suit your needs, here are some trending alternatives:
1. Character.AI
-
Family-friendly
-
No NSFW content
-
Great UI & mobile app
2. Chai App
-
Available on Android & iOS
-
Tons of user-generated bots
-
Less control over filtering
3. Pygmalion AI + SillyTavern
-
Fully unfiltered
-
Requires setup
-
Works offline with local LLMs
4. OpenAI Playground (ChatGPT)
-
Reliable for clean conversations
-
Limited in roleplay compared to Janitor
📌 For a comparison article, see: [Janitor AI vs Character AI – Which is Better?] [INTERNAL LINK]
💻 Developer & Community Tools
If you’re a developer or enthusiast, Janitor AI allows:
-
Bot creation: Customize prompts, memories, behavior.
-
API linking: Choose your preferred backend model.
-
Community uploads: Share your bot with others.
-
Third-party mods: Chrome extensions, Discord integrations
Some devs even run private versions of Janitor AI using open-source tools like:
-
JanitorAI-Local
-
Sillytavern UI
-
KoboldCPP
✅ Pros and Cons
| Pros | Cons |
|---|---|
| Deep roleplay capabilities | May violate ethical/age guidelines |
| Supports multiple AI backends | Complex setup for unfiltered APIs |
| Active community & support | NSFW misuse concerns |
| Free to use (with API) | Not beginner-friendly without guides |
📌 Conclusion (with Links Added)
Janitor AI is much more than just another chatbot it’s a powerful, flexible platform for those looking to dive into immersive conversations with fictional, realistic, or AI-generated characters. Whether you’re writing a fantasy novel, simulating a companion, or just killing time, it opens up countless possibilities.
But with great flexibility comes responsibility. Use Janitor AI ethically, protect your privacy, and respect the boundaries of content guidelines.
Want to explore more ways to leverage AI? Check out our guide on
👉 How to Make Money with ChatGPT in 2025 – 10 Proven Methods
Or visit our homepage for more trending AI tools, tech updates, and tutorials:
🌐 SpaceCoastDaily.co.uk
❓ FAQ – Janitor AI 2025
Q1: Is Janitor AI free to use?
Yes, the platform is free, but you’ll need to connect your own API key (like OpenAI, Kobold, or Pygmalion).
Q2: Is NSFW content still available?
Officially, NSFW content is restricted. However, users can still access it via third-party APIs or local setups.
Q3: Is Janitor AI safe?
It’s generally safe if you use trusted APIs and don’t share personal info. For NSFW use, caution is advised.
Q4: Can I use it without coding?
Yes, Janitor AI has a user-friendly interface. You only need to copy-paste API keys.
Q5: What is the best API for Janitor AI?
For filtered, ethical use: OpenAI. For unfiltered creative freedom: KoboldAI or Pygmalion.
-

 Tech1 week ago
Tech1 week agoWhat is Janitor AI? Features, Use Cases & How to Use It Safely in 2025
-

 news1 week ago
news1 week agoBinomo Scam Exposed: Real Truth Behind the Trading App You Must Know in 2025
-

 news1 week ago
news1 week agoChatGPT vs Google Gemini: Which AI Wins in 2025?
-
Business4 weeks ago
Why Bulk Custom Playing Cards Are the Secret Weapon for Brand Visibility and Creative Projects
-

 Gaming2 weeks ago
Gaming2 weeks agoBest Gaming Accessories Under $50 in 2025 – Ultimate Budget Gaming Upgrades
-

 Tech2 weeks ago
Tech2 weeks agoPortalar (PortalAR) Guide 2025: How AR Portals Transform Environments
-

 news2 weeks ago
news2 weeks agoJames Webb Telescope News: Exploring the Frontiers of the Universe
-
Tech4 weeks ago
Revolutionizing Marketing with AI: How Visionation Helps Brands Dominate Google Rankings